OpenLDAP is an open-source suite of LDAP (Lightweight Directory Access Protocol) application and development tools. It is a key tool to realize single sign on operation in network environment.
Installation
These packages are required for OpenLDAP to function properly:
- yum install openldap-servers
- yum install openldap-clients
Start OpenLDAP service
The init script file for OpenLDAP is slapd.
# service slapd start Starting slapd (via systemctl): [ OK ]
Check status of OpenLDAP service:
# service slapd status
slapd.service - LSB: starts and stopd OpenLDAP server daemon
Loaded: loaded (/etc/rc.d/init.d/slapd)
Active: active (running) since Thu, 08 Mar 2012 13:42:27 +0800; 1min 0s ago
Process: 1669 ExecStop=/etc/rc.d/init.d/slapd stop (code=exited, status=0/SUCCESS)
Process: 1692 ExecStart=/etc/rc.d/init.d/slapd start (code=exited, status=0/SUCCESS)
Main PID: 1722 (slapd)
CGroup: name=systemd:/system/slapd.service
â 1722 /usr/sbin/slapd -h ldap:/// ldapi:/// -u ldap
Configuration - cn=config
OpenLDAP use statically configured slapd.conf prior to version 2.3. A new run-time configuration and zero down-time configuration, cn=config introduced since version 2.3. A most notable cn=config is the configuration parameters may entered via ldapmodify or LDIF files. The changes has immediate effect without restart slapd service.
Configuration - Add cn=config admin password
The cn=config in a fresh OpenLDAP installation doesn’t has admin password. Administrator may not change OpenLDAP configuration parameters without admin password. The first task after a fresh OpenLDAP installation is add cn=config admin password.
Generate slapd SSHA password:
# slappasswd -h {SSHA}
New password:
Re-enter new password:
{SSHA}m8MhPiaG0TWmP/Ro2VcRopBqTbTm1UX1
We will use the new generated password “{SSHA}m8MhPiaG0TWmP/Ro2VcRopBqTbTm1UX1 ” in next step.
Next, determine the DN (Distinguished Name) for the database that contains the RootDN password. The RootPW (root password) may not present in fresh installation:
# ldapsearch -LLL -Y EXTERNAL -H ldapi:/// -b olcDatabase={0}config,cn=config dn olcRootDN olcRootPW SASL/EXTERNAL authentication started SASL username: gidNumber=0+uidNumber=0,cn=peercred,cn=external,cn=auth SASL SSF: 0 dn: olcDatabase={0}config,cn=config olcRootDN: cn=config
Next, add olcRootPW to olcDatabase={0}config,cn=config using shell-accessible tool ldapmodify with LDIF text:
# ldapmodify -Y EXTERNAL -H ldapi:/// SASL/EXTERNAL authentication started SASL username: gidNumber=0+uidNumber=0,cn=peercred,cn=external,cn=auth SASL SSF: 0 dn: olcDatabase={0}config,cn=config add: olcRootPW olcRootPW: {SSHA}m8MhPiaG0TWmP/Ro2VcRopBqTbTm1UX1 modifying entry "olcDatabase={0}config,cn=config"
In the above example, as soon as empty line received, the LDIF text will be processed immediately. Press Ctrl-D to end ldapmodify shell when done.
GUI tools for LDAP directory
Apache Directory Studio is a GUI LDAP browser and client to manage LDAP directory. It save lot of time and effort to use ldapmodify managing the directory entries.
Manage cn=config using Apache Directory Studio
Create LDAP connection in the studio:
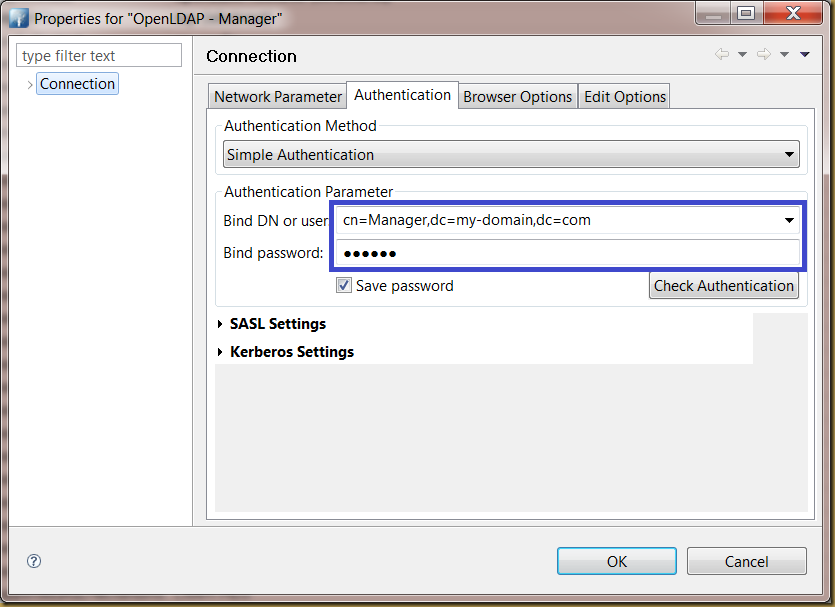
Enter authentication information for the connection:
Enter cn=config to BaseDN text box:
Commit the changes by pressing OK button. You may open the connection and start browsing the OpenLDAP configuration parameters.
Configuration: olcDatabase
You may start configure a new LDAP directory once OpenLDAP service is up and running. The olcSuffix parameter let you specify a unique identifier for the directory. olcRootDN specify the supervisor for the directory.
A olcRootPW may be added to secure the directory from anonymous changes.
Browse OpenLDAP directory as Manager
Define a new OpenLDAP connection using RootDN to access a fresh LDAP directory:
Connect to the LDAP directory shows an empty directory:
Add an initial entry to LDAP directory
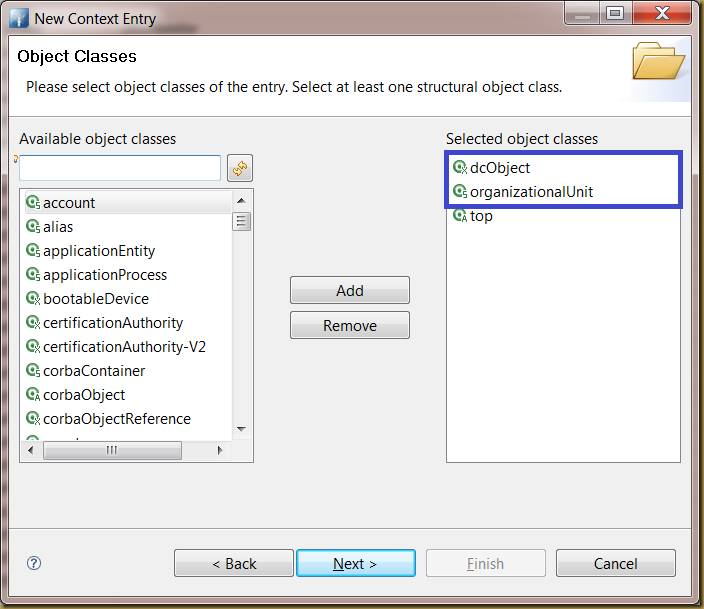
Use “New Context Entry…” to create an initial entry to LDAP directory:
First, define a new object using dcObject and organizationUnit classes:
Next, enter a DN for the object:
Supply a ou value to identify the entry:
The following diagram shows the newly created object:
Flooding the LDAP directory
You may start enter the LDAP objects to the directory:
Reference
- OpenLDAP. URL: http://www.saruman.biz/wiki/index.php/OpenLDAP











2 comments:
admin
i need your help. i try as a year install to the CUDA programme but still replay error massage please what happen.please ( My VGA GTX 460)
root@bt:~/pyrit/cpyrit_cuda# python setup.py build
running build
running build_ext
Skipping rebuild of Nvidia CUDA kernel ...
Building modules...
building 'cpyrit._cpyrit_cuda' extension
gcc -pthread -fno-strict-aliasing -DNDEBUG -g -fwrapv -O2 -Wall -Wstrict-prototypes -fPIC -I/usr/local/cuda/include -I/usr/include/python2.6 -c _cpyrit_cuda.c -o build/temp.linux-x86_64-2.6/_cpyrit_cuda.o -Wall -fno-strict-aliasing -DVERSION="0.4.1-dev (svn r308)"
gcc -pthread -shared -Wl,-O1 -Wl,-Bsymbolic-functions build/temp.linux-x86_64-2.6/_cpyrit_cuda.o -lcrypto -lcuda -lz -o build/lib.linux-x86_64-2.6/cpyrit/_cpyrit_cuda.so
/usr/bin/ld: cannot find -lcuda
collect2: ld returned 1 exit status
error: command 'gcc' failed with exit status 1
==========
please give to your e mail ID
admin
CUDA core error please help me
root@bt:~/pyrit/cpyrit_cuda# python setup.py build
running build
running build_ext
Skipping rebuild of Nvidia CUDA kernel ...
Building modules...
building 'cpyrit._cpyrit_cuda' extension
gcc -pthread -fno-strict-aliasing -DNDEBUG -g -fwrapv -O2 -Wall -Wstrict-prototypes -fPIC -I/usr/local/cuda/include -I/usr/include/python2.6 -c _cpyrit_cuda.c -o build/temp.linux-x86_64-2.6/_cpyrit_cuda.o -Wall -fno-strict-aliasing -DVERSION="0.4.1-dev (svn r308)"
gcc -pthread -shared -Wl,-O1 -Wl,-Bsymbolic-functions build/temp.linux-x86_64-2.6/_cpyrit_cuda.o -lcrypto -lcuda -lz -o build/lib.linux-x86_64-2.6/cpyrit/_cpyrit_cuda.so
/usr/bin/ld: cannot find -lcuda
collect2: ld returned 1 exit status
error: command 'gcc' failed with exit status 1
Post a Comment